blog
What is
Cyber Range?
- Types and Use Cases
A hyper-realistic simulation platform designed for modern teams to learn the best Infosec skills by fighting real-world cybersecurity attacks
What is Cyber Range?
As cyber threats are evolving, the teams tasked for cyber defense are not keeping up with the demand and finding it hard to attract the right Infosec staff to protect their digital infrastructure and data.
The huge deficit of cybersecurity professionals is a major reason why every Industry and government group is finding it hard to deal with the rising levels of cybercrime.
The fundamental causes for this skill gap are myriad, and the major contributor has been the traditional approach of teaching cybersecurity that is more theory and product-driven with less spotlight on teaching genuine real-life mitigation techniques.
Cyber Range on the other hand is more versatile and provides real-life exposure to cyber-attacks for better learning outcomes and incident response capabilities. It is a hyper-realistic simulation platform that mimic's every major digital infrastructure and attack scenario — so participants can practice and improve their skills in a controlled environment and learn how to mitigate attacks before taking up the final role in any organization.
Cyber Range is more like a Flight simulator that artificially mimics aircraft flight and the environment in which it flies, widely being used for pilot training, research, and design purposes. Similarly, it also reduces the chances of accidents, improves response capabilities, and reduces the cost of training in a real environment and setup.
Types of Cyber Range
Generally speaking, there are 4 types of Cyber Ranges. Though they all provide similar kinds of services. The type of Cyber Range becomes more significant when they are mapped against the use cases for which they will be purchased and deployed.
Simulation Cyber Range- This is the most preferred versions of Cyber Range across the world where the primary use case is skill development & infrastructure simulation. The objective here is to replicate the real-world traffic of an enterprise network in a simulated environment with the help of virtual machines. How closely one can match the real-world traffic (attack, defense, and normal traffic) is the main focus area in such type of Cyber Range.
Pros -
- Easy and Fast to deploy.
- Low maintenance and operational cost.
- Easy to upgrade and update the setup.
- Cheaper than Overlay Cyber Ranges.
- Can be deployed on general purpose servers supplied by vendors like Dell/HP/IBM etc.
Cons -
- It is still a simulated environment and not the real one.
- Performance issues may be experienced due to underlying Virtualization Infrastructure.
Overlay Cyber Range - They are designed on top of real networks, servers, and storage. They are almost a replica of a given enterprise network where everything is as close as the real world except they do not receive real-time production traffic.
Pros -
- High fidelity* as compared to other solutions.
- Fast and predictive
*fidelity- the degree of exactness with which something is copied or reproduced.
Cons -
- High Cost of acquisition.
- High maintenance cost.

PurpleSynapz Co-Founder & CTO, Ashok at NIT Manipur (Nov 2013)
Emulation Cyber Range - This type of range is an interconnection of multiple closed networks. Generally, it is used along with traffic generators so as to generate any kind of traffic that is technically possible in a closed environment.
Pros -
- Quality & quality of traffic is excellent.
- Application stress testing can also be performed.
Cons -
- It offers moderate fidelity as the traffic is coming from emulated software.
- Cost of traffic generators are generally high.
Hybrid - As the name suggests it is a combination of any of the above Cyber Ranges.
Pros -
- Flexibility to choose what you want and how you want to use.
Cons -
- Complex integration process.
- Higher maintenance and operational cost.
Cyber Range Use Cases
Cyber Ranges are generally used for the following use cases. End customer/user has to decide how they want to invest and use the Cyber Range.
Training platform
One of the most common use of Cyber Range is to train participants of any experience in a simulated environment. The training usually focuses on following domains:
Red Team, Blue Team, Incident Response, Threat Hunting, Cyber Forensic, Red Vs Blue Game, CTF (Capture the flag).
Product Security Testing platform
I remember working on a client project where we were engaged in a VAPT exercise. We were cautious while performing pen-testing on the production network as any critical bug/vulnerability would have caused a serious damage to the system. But considering the situation when a hacker tries to breach, he shows no mercy. They will continue with their attacks till the last possible stage.
With Cyber Range platform, the Red Team has a complete freedom to launch multiple attack scenarios without worrying about the demage, as everything they test is the replica of real infrastructure present in their organization. This allows them perform rigorous attacking scenarios to test how it stands against real-life cyber attacks.
Product development platform
So you want to create a new Proof of concept and this new application/tool must work seamlessly in the production network with all the security controls in place. Well, you now have access to a simulated environment where any new product can be developed, tested,, and integrated with other tools and applications.
Compare this requirement with something like introducing a new ball. Let the players play the game and it will automatically demonstrate the capability of the new ball.
Skill assessment platform: Finding the right talent and training them has been the major challenge for every Industry and government organizations. Such pursuit requires time and effort, and considering the skill-gap present in the cybersecurity domain, the companies all around the world are finding it hard to match the rising level of cyber threats.
To attract best talent, Cyber Range can be of huge relief, this platform can allow teams to assess specific skills and response time in a controlled and hyper-realistic environment. The practice allows right talent onboarding without wasting time in traditional assessment methods.
Simulation platform. - Customer creates the digital twin of their IT Core Infrastructure and uses the same for skill development customized for their Infrastructure. The simulation platform also offers Cyber Security posture enhancement. For example, the customer/partner can pick up the latest malware relevant for the customer and test whether the security control devices are able to protect against the malware. If not, fix it inside the Range and then port the solution into the production network. And also stress test the SIEM co-relation rules and see if they are effective or just kept at a bare minimum (default) working condition.
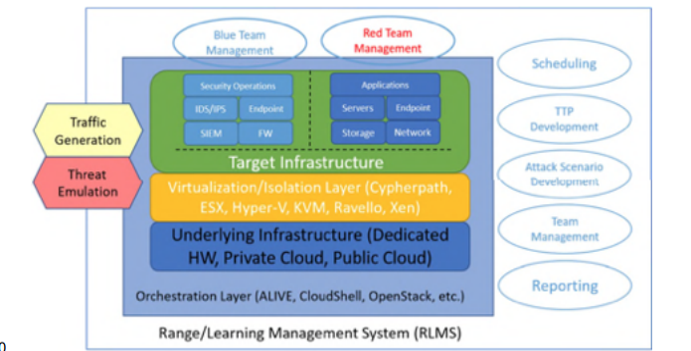
Sample Architecture of a Cyber Range.
Cyber range consists of following main components.
- Base Infrastructure -(Physical Hardware, Public Cloud, Private Cloud)
- Virtualization Layer - (Cloudshell, Openstack, VMware ESXi, Microsoft Hyper-V,XenServer, KVM)
- Virtual Machines - (These Virtual machines represents real world server,router,firewall,web applications, Attacker machines and other core devices of a typical Enterprise.)
- Normal User traffic - Traffic that is normal in nature such as web browsing, ping, ssh, mail, syslogs, dns, ntp etc)
- Application traffic - This is a traffic between normal and malicious users who are trying to access any web application server in Cyber Range.
- Malicious traffic - This is the traffic that is generated by malicious users. The purpose of such traffic is to bypass the security control devices and attack the servers and endpoints.
- Attacker machines - These are external or internal devices that try to gain unauthorized access to applications and other core devices.
- Security Control Devices - These are the devices which will try to protect the applications and core devices from un-authorized access from malicious users.
Here are some of the most common Security Control Devices that are part of Cyber Range solution.
- Firewall
- IDS
- WAF
- SIEM
- Proxy Server
- Sandboxing
- Email Protection
- End Point Protection
Things to consider while investing in Cyber Range Products.
Here are a few important FAQs that will help you make an informed decision about deploying Cyber Range.
- What is the primary use case for which you are planning to invest in Cyber Range?
Answer - Training, SOC use cases, Red Teaming, Skill assessment, Capture the Flag (CTFs), custom requirement, etc. - Will the Cyber Range be heavily utilized?
Answer - Will the Range be used 24x7, Twice a week, a few days in a month, Only during a specific period, etc. - Shall I go for a cloud or on-premises solution?
Answer - If the utilization is more then it would be economical to deploy an on-prim solution else pay as you go model is good. - Which all OEM tools are supported in Cyber Range Lab?
Answer - Go for a solution that offers maximum customization. Choose the vendor and OEM should be able to integrate the same in Cyber Range Lab. - Will I be using my own resources to manage and run the Cyber Range Lab?
Answer - If the use case is basic training, then you need not worry as most of the Cyber Range labs do not need a senior dedicated engineer to run the Lab. However, If your use cases are more complex then you may want to hire a senior resource to manage the Cyber Range lab.
- How to add custom scenarios in Cyber Range?
Answer - Look for a product that allows your team to add scenarios based on data and information available with your team. With little or no intervention from the OEM vendor, your team will be able to add more scenarios. - Who will provide the training content?
Answer - Needless to say Cyber Ranges are complex products and some amount of hand-holding would be needed before engineers start using them to learn new skills. - You may want to look for an integrated solution where course content is also part of the final solution.
- How many people can be trained in a single batch?
Answer - You need to check how many people can utilize the Cyber Range platform at one go. Generally speaking 10-15 engineers in a single batch is considered a good choice.

.svg)